I was explaining something in probability theory to somebody last night, and I offhandedly said the following remark:
You know, it’s interesting what sorts of mathematics come up. For example, a usual exercise in undergraduate probability is the following: Flip a coin repeatedly until a heads comes up. What’s the expected number of coin flips required?
The person asked me what the number was, and I realized that I actually didn’t know. I gave an offhand guess of three, since we’re asking about a very particular sequence of coin flips (which has exponentially small density in the measure of all sequences of coin flips, and so it should be small). I sat down to work on it before bed, and rather quickly derived the following expression.
Let 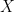 be the random variable in
be the random variable in  with the interpretation that
with the interpretation that  if the
if the 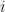 th coin flip in a sequence of flips is a head after
th coin flip in a sequence of flips is a head after  tails. It’s straightforward to calculate
tails. It’s straightforward to calculate ![\Pr[X = i] \Pr[X = i]](http://s.wordpress.com/latex.php?latex=%5CPr%5BX%20%3D%20i%5D&bg=ffffff&fg=000000&s=0) — assuming we’re flipping a fair coin, the probability of getting
— assuming we’re flipping a fair coin, the probability of getting  tails followed by a single head is
tails followed by a single head is  . This means our expected value will be
. This means our expected value will be ![E[X] = \sum_{i=1}^{\infty} i \Pr[X = i] = \sum_{i=1}^{\infty} i 2^{-i}. E[X] = \sum_{i=1}^{\infty} i \Pr[X = i] = \sum_{i=1}^{\infty} i 2^{-i}.](http://s.wordpress.com/latex.php?latex=E%5BX%5D%20%3D%20%5Csum_%7Bi%3D1%7D%5E%7B%5Cinfty%7D%20i%20%5CPr%5BX%20%3D%20i%5D%20%3D%20%5Csum_%7Bi%3D1%7D%5E%7B%5Cinfty%7D%20i%202%5E%7B-i%7D.&bg=ffffff&fg=000000&s=0)
And, wait a minute, but this sum is not trivial to evaluate! At first I did what any self-respecting mathematician/computer scientist would do (i.e. HIT IT WITH YOUR HARDEST SLEDGEHAMMERULTRATOOL AND DYNAMITE THE PROBLEM TO ACCESS IT’S SWEET GOOEY INSIDES) and applied generating functions.

MMMMMMMMMMMMM
This (alas) didn’t work and I fell asleep dejected.
And I woke up with the cutest solution!
To begin, here’s a secret that your math teacher just won’t ever bloody tell you:
(1) Every inequality/sum/identity in the history of mathematics just comes from writing the same thing in two different ways.
Of course, with our friend hindsight bias this is obvious — once we have the identity  in front of us, it’s easy to say “oh, well of COURSE
in front of us, it’s easy to say “oh, well of COURSE  , it’s so obvious, duh!”.
, it’s so obvious, duh!”.
Now, here is a second secret that your math teacher won’t ever bloody tell you:
(2) Every result ever obtained in mathematics can be broken down to a sequence of tiny, local, or otherwise easy steps.
When you say something as simple as I did in these two principles the questions of mathematics suddenly become significantly less daunting. To illustrate both of these principles, I’ll use them to evaluate our sum  from the probabilistic puzzle above. First, let’s recall what an infinite sum actually is, as it’s kind of easy to forget: the sum
from the probabilistic puzzle above. First, let’s recall what an infinite sum actually is, as it’s kind of easy to forget: the sum
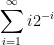
is really defined as a limit of partial sums

So, applying our first principle from above, we’re going to rewrite  as another function
as another function  so that we can actually evaluate the limit above.
so that we can actually evaluate the limit above.
Now, how do we do this? First, just to simplify notation for ourselves, let  Let’s apply our second principle from above — what are some really stupendously obvious facts about the sum
Let’s apply our second principle from above — what are some really stupendously obvious facts about the sum  ? Well, since it’s a frigging sum, we know that
? Well, since it’s a frigging sum, we know that

Alright, here is a start. If we can apply our first principle to the sum 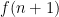 and write it down in another way then maybe we’ll end up somewhere interesting. Well, what about this sum? Let’s write it down explicitly, so that we can actually see some of the structure of the terms. I’m also going to make the substitution
and write it down in another way then maybe we’ll end up somewhere interesting. Well, what about this sum? Let’s write it down explicitly, so that we can actually see some of the structure of the terms. I’m also going to make the substitution 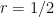 and instead write
and instead write

Time for a side rant. Now, a math teacher, jerks as they are, will tell you to do this kind of substitution because your result is more general (or, even worse, tell you nothing at all, leaving you swimming in a soup of variables/indeterminates with no flotation device).

Everyone in any math class, ever. THE OCEAN IS VARIABLES
As usual, this is the correct information but stated in a way so that humans can’t understand it. Another way to say this “generality” assumption is, simply, people hate magic numbers! Notice that NOTHING! about the sums we’ve considered so far have needed the 2 to be there (other than the fact that our problem happens to be about coins). Well, if there’s no reason for it to be there, then why should it be there? The sum  is even a bit easier to swallow visually. Anyways, side rant over.
is even a bit easier to swallow visually. Anyways, side rant over.
Back on track, here are the sums  and
and 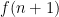 , both written down explicitly:
, both written down explicitly:
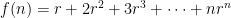
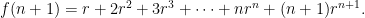
Well, recall that I said that we were trying to rewrite 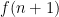 in a way other than
in a way other than

Applying our first principle — and this is really the leap of intuition — let’s just transform  into
into 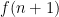 in another way! How? Well, multiply
in another way! How? Well, multiply  by
by  and compare it to
and compare it to 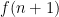 :
:
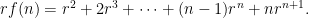
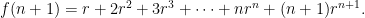
We’ve almost got 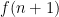 ! The only thing that’s missing is a single copy of each term in the sum! Phrased mathematically, we now have the identity
! The only thing that’s missing is a single copy of each term in the sum! Phrased mathematically, we now have the identity

Now, the sum 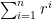 is a geometric sum which has a simple formula (fact: this simple formula can be derived in a way similar to our current investigation):
is a geometric sum which has a simple formula (fact: this simple formula can be derived in a way similar to our current investigation):

So, substituting in this new simple formula gives

and then, finally finishing our application of the first principle, we can apply our early “stupid” identity for 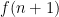 and get
and get

The rest is algebra/boilerplate. Collecting the  terms on the left hand side, we get
terms on the left hand side, we get

then dividing both sides by 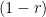 finally gives
finally gives
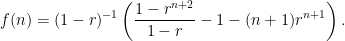
Taking the limit as  and using our knowledge that
and using our knowledge that 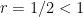 , we see that the terms involving
, we see that the terms involving 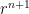 will disappear. This leaves
will disappear. This leaves

Substiting in 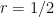 , we get
, we get
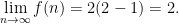
And we’re done. In expectation, you will see a heads after 2 coin flips.
You see, math is not mystical. Unless you’re a Newton or an Euler (viz. an absolutely genius), math proceeds pretty much the same for everybody. There are underlying principles and heuristics that help you do math that every established mathematician actually uses — the secret is that no one ever tells you them. Of course, I have a sneaking suspicion that this due to the fact that our high school math teachers don’t actually understand the principles themselves (while this may seem like a bit of an attack, I did graduate with people who were going to be math teachers. Most of those people should not have been math teachers).